Since – as has been recently noted – Moose are ruminants, here are some thoughts I have been having on addressing cybersecurity in industrial control systems.
The articles that end up instantiated as Moose markings are by nature and fact often completely off the political reservation. This topic does have significant political implications, though, as the stability of these systems both at home and abroad pose tactical and strategic challenges to social structures and political balance. To that point it is in fact very much a matter of interest for all members of our shared social experience.
The following is a set of slides describing a program that has been developing over this year.
The premise of the program is that there are hundreds of thousands of facilities in the United States alone where cyber systems control physical processes, and where the intentional subversion of these cyber systems could cause human and social harm, and that there is a need to secure these systems in a timely and effective fashion.
This particular set of slides is made for the Water sector, where more than 18,000 US water systems remain largely unaddressed from a cybersecurity perspective.
I will be interested to see how much sense this makes to all of you. There are parts of it that I believe may cause some interesting debate, but I will let you decide which those might be. ;~)

“ICS” = Industrial Control Systems”

LIGHTS is a program run under Energysec, a 501(c) non-profit created by cybersecurity experts from the electric sector. The founders and board of LIGHTS consist of representation from the vendor, service provider, asset owner and academic segments.
The charter of LIGHTS is to provide highly-deployable low-cost cybersecurity options to ICS facilities. The purpose of these solutions is to allow for persistent and comprehensive visibility into the state and behavior of the cyber assets that compose the industrial control system. The specific method currently is based on Open Source (free and community maintained) sensor devices monitored by LIGHTS-certified Managed Security Service Providers (MSSPs).

LIGHTS was created to address the reality that the majority of industrial facilities do not have the expertise or resources to adequately address the risk to their cyber systems. Many of the individuals who build and operate these systems in small-to-medium environments have voiced their concern and requested standardized programs.

LIGHTS itself is – well – a light organization. The board certifies vendors and service providers to offer a standard menu of options. The ground-level option is an Open Source Sensor installed on a single ethernet port of the core switch on the subject facility’s network. This device is connected over an encrypted connection to the MSSP’s Security Operations Center where analysts provide constant monitoring and response capability. As options the facility can choose not to have a managed service and monitor their own Sensor (the Basement option) or upgrade to commercial products.

In the Water and Wastewater sector all of this is necessary because – like in other sectors – it is virtually certain today that every cyber device deployed has known or unknown security vulnerabilities which could be exploited. The threat of these vulnerabilities rises as a function of time, while the expertise to address it is generally not available to water operators.
The existing standards – ANSI/AWWA G430-09 and ASME-ITI/AWWA J100-10 Risk Analysis and Management for Critical Asset Protection (RAMCAP) Standard for Risk and Resilience Management of Water and Wastewater Systems – already require water operators to account for hostile intention and provide safe service under those conditions. These and other regulations will increasingly require water facility operators to demonstrate control over cyber systems while these systems are under active attack, a necessary goal which is not foreseeably within the grasp of a majority of them.
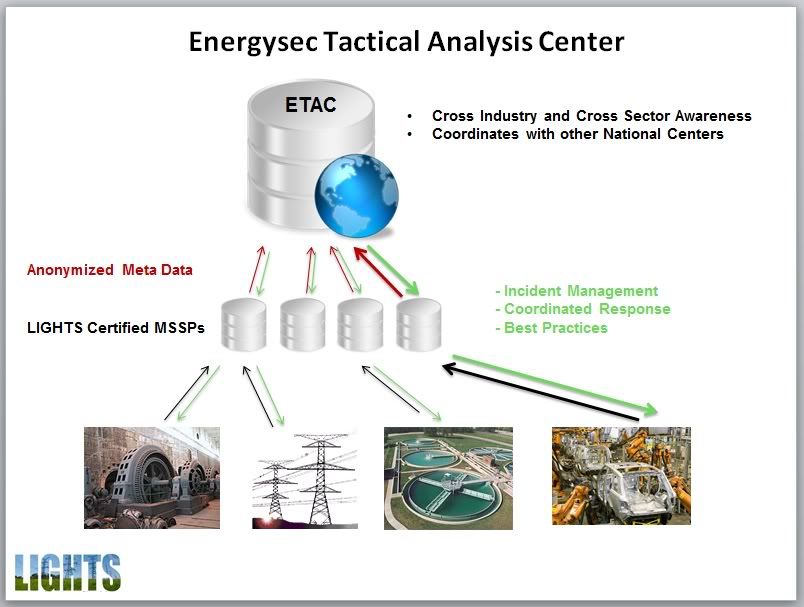
Let’s look at the technical shape of the LIGHTS system, starting at the largest scale and drilling down.
At the top is the Energysec Tactical Analysis Center. TAC draws data from LIGHTS MSSPs in all sectors in a consistent format. As appropriate this information is anonymized meta information which does not reveal the confidential information of either the constituent organizations or of the parties to which they are responsible to, such as ratepayers.
TAC correlates and processes this data and produces actionable intelligence for use by member organizations. Energysec TAC also coordinates with other government and private centers, integrating that intelligence for it’s membership’s benefit while providing appropriate information to those centers.
TAC provides appropriate guidance to constituent organizations, including assistance with Incident Management at individual facilities, Coordinated Response during widespread and active cyber threat and current best practices.
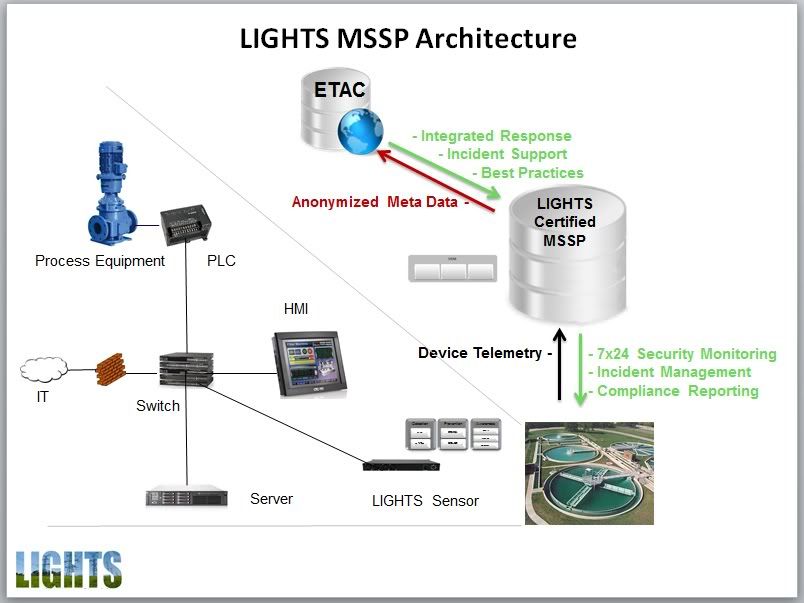
A deployment is based on a LIGHTS Sensor getting installed on a “promiscuous span port” on the existing ethernet switch on the subject facility’s control network. This Sensor analyzes all network traffic, creating a baseline of normal conditions against which to detect the anomalous behavior characteristic of an unauthorized intrusion. The LIGHTS Certified MSSP for a given facility monitors the Sensor over an encrypted channel in 7×24 Security Operations Center. The SIEM technology required for LIGHTS MSSP certification includes the capability of automatically alerting on deviations from the facility’s security policies and/or established behavioral norms.
LIGHTS Sensors are based on the Open Source SIEM (OSSIM). OSSIM is the most commonly used SIEM technology and does not introduce product or licensing costs into the base LIGHTS offering. LIGHTS Sensors include an integrated suite of Open Source cybersecurity tools including Intrusion Detection and Vulnerability Assessment to provide a consistent and complete operational framework.
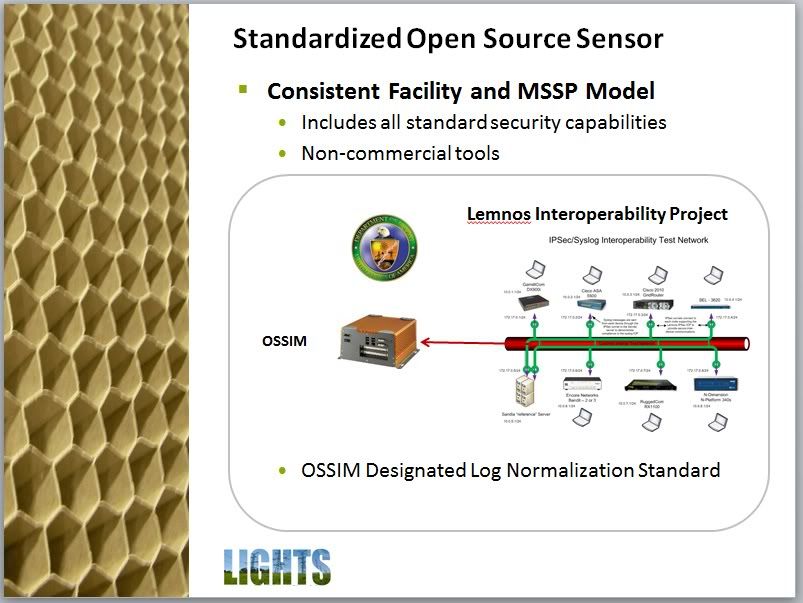
Lemnos was a DoE-funded initiative intended to establish and demonstrate multi-vendor interoperability among control system cybersecurity components. Encryption and event message standards are the two main goals of the project.
The initial Event Messaging effort focused on pushing vendors to conform a set of syslog event messages to a common standard. However, coordinating vendor development is problematic at best and much installed equipment using existing messaging may not be updated for an extended period of time.
The Lemnos project has solved this issue by designating the Open Source SIEM (OSSIM) as the standard collection method for interoperable event messaging. OSSIM is maintained by AlienVault and the Open Source community and is used at more than half of all SIEM deployments globally, providing a stable platform for the purpose. OSSIM includes a Standard Event Taxonomy: event messages such as syslog produced by vendor equipment are sent to OSSIM and automatically mapped to this Standard Event Taxonomy, allowing for standardized policies and reporting.
This common event taxonomy is an essential component of the LIGHTS framework, allowing constituent facilities to produce standardized data and LIGHTS MSSPs to provide consistent
and economical services. This standardization also supports the infrastructure necessary for ETAC to provide standardized responses and recommendations to constituent organizations, increasing effectiveness and efficiency of the national cybersecurity management and response system.

With its consistent and modular structure, LIGHTS provides an option which can scale to address the risk over reasonable timeframes. The framework lends itself to providing forensic evidence of regulatory compliance and is flexible enough to reflect evolutions in regulated requirements.
Most importantly, LIGHTS provides automated visibility into system behavior and the deviations that can indicate loss of control through attack, equips facilities with a response capability and allows them to engage with cross-industry centers of awareness and expertise.
17 comments